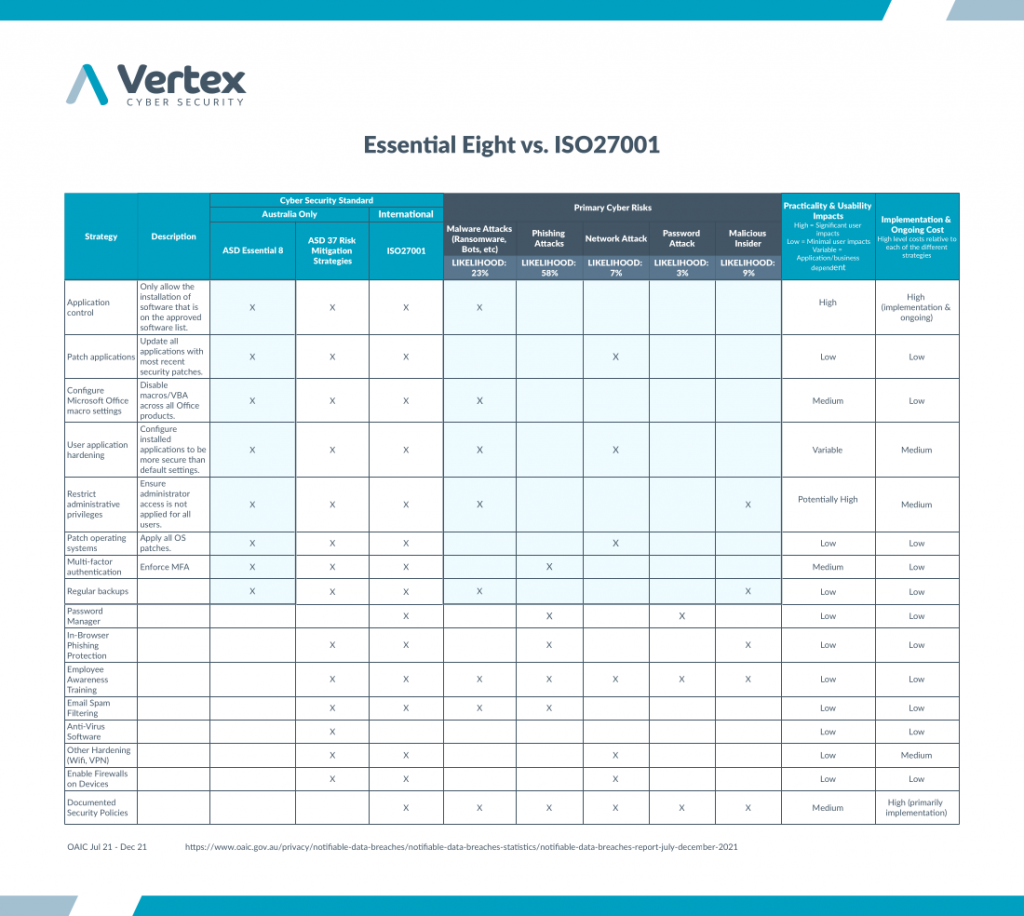
The Essential 8 and ISO 27001 are two different approaches to information security management.
The Essential 8 is a standard produced by the Australian Government – ASD (Australian Signals Directorate) and ACSC (Australian Cyber Security Centre). It is the top 8 Cyber Protections from their list of their 37 Cyber Protections (https://www.cyber.gov.au/acsc/view-all-content/publications/strategies-mitigate-cyber-security-incidents).
ISO27001 is a standard produced by the ISO (International Organization of Standards). It involved more than 100 Cyber Experts sharing their experience to develop a list of 114 Cyber Protections (controls).
Essential 8 and ISO27001 are both Cyber Standards with lists of protections (controls) and were developed from Cyber Experts with experience in dealing with Cyber attacks. If we compare the ASD/ACSC 37 against the ISO27001 there is a lot of overlap. ISO27001 has more documentation and processes that enable good Cyber Protection such as a list of all your assets so you know what you are protecting from Cyber attack.
Alternatively Essential 8 is a smaller list with a focus on malware protection. Compared with ISO27001 it is missing a lot (Refer to picture) and can appear a bit malware protection focused.
Essential 8 is aimed as a minimum for government businesses so it wasn’t built to be business friendly. Essential 8 also has conflicting protections (patching vs application allowlisting) which increase IT management costs beyond acceptable for many businesses. This is why they had to introduce a maturity level to allow reduced protections for each of the 8 Cyber Protections.
Where possible we would recommend looking at ISO27001 or ASD/ACSC 37 over Essential 8 as they are more comprehensive. Where Essential 8 is required, as a business, you may not have the choice but if you have the capacity we would still recommend applying some or all of the controls of ASD/ACSC 37.
If you need some help implementing or discussing Essential 8, ASD/ACSC 37 or ISO27001 contact the Cyber Experts at Vertex Cyber Security.